...but Linux experienced.
Having recently purchased a Nexus 7 32GB (2013 model) as my very first Android mobile device, I am finding that the information on how to gain complete control is both all over the place and supposes you're already familiar with the whole rooting process, which I'm not. Therefore, I'm going to write yet another step by step guide on what you need to do, to be able to remotely ssh into it and run a shell as root, which, IMO, is the one stage where we can pretend that we are actually running a GNU/Linux system under the hood and get things done.
Incidentally, if you don't care about commandline Linux, this process will also grant you full control and let you do whatever you please with the device.
Being a complete Android noob, I will also make sure not to skim over all the
"Oh, but you're supposed to know that already!" details, so that you will hopefully be as successful as I was, in rooting your device. On the other hand, I will assume that you are somewhat familiar with Linux. But don't let that worry you as the Linux specific items will come at the very end, at which stage your device will already be fully rooted.
Finally, since it's somewhat convenient, I will be using Windows as the platform we'll use to communicate with the Nexus 7 during this process, and I'll assume that you are familiar enough with it to find your way around the Device Manager, manual driver installation and the Windows command line.
Why *I* want to root my device
I'm not going to venture a guess as to what your reasons are for rooting
your device. But one of the first reasons I have, in a very long list, is to be able to edit the device's
/etc/hosts and get rid of most of the ads and unwanted trackers, which every other device and computer that I have doesn't have to put up with, through a skilful use of the ever so awesome
WinHelp 2002 host file. And yeah, I know there are other ways to block ads, but the
/etc/hosts method is still the simplest, most universal and effective way, since it'll block ads for all apps running on your system, rather than the ones in a single browser application.
Now, the ironic part is: the reason I purchased a Nexus 7 in the first place is through revenue that I got from placing ads on a
successful little web site (Hurray, for unexpected disposable income!).
Am I really going to bite the hand that feeds me? Watch me!
Besides eliminating ads, there are of course plenty of other reasons to want to root your device, such as recompiling and running your own custom kernel (we'll come to that
in a next post), but we might as well start small, by improving our mobile surfing experience.
What the other guides omit to tell you...
For the most part, I am going to follow the video guides at
xda-developers and most specifically, the third and second to last from this link. Oh, and if you want a less verbose, yet noob friendly and up to the point guide, I can only recommend the "
How to build Cyanogen for Nexus 7 2013" one, as it has a very easy to follow section on rooting. Still, part of these guides suppose some familiarity with the process and omit some important details that you may be interested in knowing beforehand, such as:
The internal name of the Nexus 7 2013 platform is 'flo'
This might be relevant if you are flashing an Android image file that came from a website that isn't dedicated exclusively to the Nexus 7 2013. If you do that, you may want to check that
'flo' is mentioned somewhere in what you're looking at. Alternatively,
'msm', which is the development branch for the 'flo' platform might be a good indicator. Remembering these two can be a good way of avoiding looking at data that is only relevant for the "old" Nexus 7, or other incompatible Android hardware.
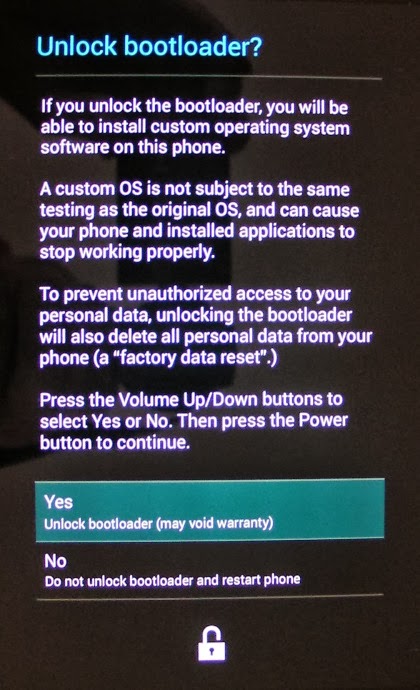
You are going to lose all your data!
More specifically, as soon as you unlock the device, which is pretty much the first step invoked in rooting, your device will be completely reset to factory settings.
In the notice they display when you do that (see screenshots below) Google say that this is to prevent someone who got unwarranted access to your phone from accessing your personal data (which is probably only a half truth, but hey...).
My advice then is: if your device is new, you want to root it as soon as possible, so that you don't have to go through the pain of restoring your apps, settings and personal data.
Then again, if you have let some time pass and installed a few things, provided you did set the device to use your google account for backup, a lot of it will be restored automatically as you re-indentify yourself after unlock. Especially, all the apps you have installed, whether free or not, will be re-downloaded and re-installed. Also,
if you're lucky, some of the customization and personal data files associated with them
may be restored... though you shouldn't really count on that and take your precautions.
But really, the less customized your device is before you root it, the better. Before attempting this procedure then, you probably want to back up as much as you can... though of course, it takes a rooted device to be able to perform a comprehensive backup of your data! As if we needed more reasons to want to root our device early.
As I assume that you are as new to the process as I was, here is a quick overview of the steps we are going to follow:
- Enable Developer access on your device - this will allow to connect your Nexus 7, through USB, to the Android debug console as well as the boot/flash utility. We'll need this to unlock the device and flash the custom (non Google) recovery image, that'll help with installing root access
- Install the Developer tools on your PC, so that you can communicate with your Nexus in developer mode.
- Unlock the stock bootloader, so that it will let you flash a non-stock recovery image. This is also the process that resets your device and data to factory settings.
- Install (flash) a custom recovery image - This will allow the installation of the binary that will supervise the granting of root access to applications (SuperSU).
- Boot into that recovery image and install (flash) the SuperSU system binaries and deamon.
- Reboot the device into standard operation mode, and install the SuperSU app. (SuperSU comes in two parts: A regular "client" app, that can be
downloaded from the App Store, and a system executable part that needs to be installed separately into the flash filesystem).
- Install Busybox
- Install an SSH server
- Customize our GNU/Linux system, including
/etc/hosts.
Enabling Developer access
So you've backed up whatever you could and accepted the idea that your Nexus will be restored to the clean slate state you found it right after you purchased it. Good.
The first thing we need then is enable developer access, which is disabled by default. To do that, you need to navigate to "Settings" → "About Tablet" (at the very end) and tap the "Build number" section 7 times. Why 7 times? Who knows...
Once you do that, you will get a small prompt indicating "You are now a developer" and after that has occurred, if you go back into the Settings menu, you will see a new "{ } Developers options" category. There, you will find a bunch of additional parameters that you can modify, that may come handy if you do development, but the only one we need right now, under the "DEBUGGING" section, is "USB debugging". So please go ahead and tap that one.
As soon as you do that, you will receive a warning about "USB debugging being intended for development purposes only", which you should accept. This should lead to the following checkmark being displayed:
Installing the USB driver and developers tools
Unfortunately, even as it is WinUSB based, the current version of Android is not
WCID enabled (but I'm working on that!), so that means you need to
manually install some drivers, to be able to communicate with the device in debug mode.
You should therefore head to
http://developer.android.com/sdk/win-usb.html click the "Download Google USB Driver" button, then pretend you accept whatever agreement they want you to agree by not reading it (so that you can feign complete ignorance of the terms if you break them, which I hear is how EULAs work these days) and unzip the files into an
usb_driver\ directory somewhere.
Now, you should connect your device to an USB port on your Windows machine. Windows will try, and fail, to locate a driver for the new debugging USB interface, at which stage you should select the "Nexus 7" unrecognised device in Device Manager, select install driver, and point to the
usb_driver\ directory you previously extracted.
Once you have done that, you should see something very similar to this:
All that is left, with regards to the developers tool installation, is to go to
http://developer.android.com/sdk/index.html and Download the SDK ADT Bundle for Windows (about 450 MB in size). Depending on whether you picked the 32 or 64 bit version, you should end up with a zip file such as
adt-bundle-windows-x86_64-20130917.zip which you can then extract somewhere like
D:\Android\adt-bundle-windows-x86_64-20130917\.
Unlocking the bootloader
The only thing we are really interested in package above are the
adb.exe (Android Debug Bridge - The application that communicates with the Android OS in debug mode) and
fastboot.exe (The application that communicates with the bootloader) and that are located in the
sdk\platform-tools\ directory. That's right; we downloaded more than 450 MB worth of junk just to access a couple of executables that don't even occupy 1 MB worth of space... talk about bandwidth wastage! (if you are concerned about this, you may want to look for smaller unofficial packages containing only
adb and
fastboot, or recompiling these from git)
Next, you should open a command prompt into your
sdk\platform-tools\ directory and issue:
adb start-server
The command window will display the following:
D:\Android\adt-bundle-windows-x86_64-20130917\sdk\platform-tools>adb start-server
* daemon not running. starting it now on port 5037 *
* daemon started successfully *
D:\Android\adt-bundle-windows-x86_64-20130917\sdk\platform-tools>
And you will also receive a request similar to this one on your device, which you should accept:

Once you have accepted the request, you will get a short message on the top status bar, indicating "USB debugging connected". Then a persistent USB debug icon, similar to the one displayed on the left, will appear in the top left corner.
The next command we want to enter, in our command prompt, is:
adb reboot bootloader
Your Nexus will now reboot in bootloader mode and once that is done, you should see a screen similar to this one, indicating "LOCK STATE - locked":
Note 1: If needed, you can use Volume Up/Volume Down to select the option highlighted at the top, and press Power to execute that option.
Note 2: You can also enter the bootloader without using the
adb command, by powering your table off, and then pressing Volume Down while powering it up.
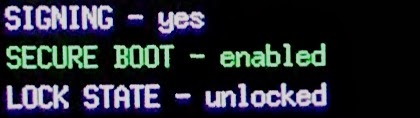
Of course, we're going to change that LOCK STATE. To do that, and since we are in bootloader mode, we can use the
fastboot command:
fastboot oem unlock
You will get a warning similar to this:
Use Volume Up/Down to select "Yes" and press the Power button. It should return to bootloader menu, but this time you should see "LOCK STATE - unlocked":
Now, you can now reboot your device by issuing the following:
fastboot reboot
Note: Because you unlocked the bootloader, the device will now reset to its factory settings. This is the part where you lose ALL YOUR DATA AND CONFIGURATION.
Installing the TWRP custom recovery image
Make sure your device boots properly, and recreate your account.
You probably also want to take some time to let the backup process reinstall your apps, as well as
manually download and reconfigure whatever personal settings and files you did backup, before you unlocked the bootloader. The rest of our operations here should not affect this data.
While your Nexus is being restored, you also want to download the following 2 files:
- The latest TeamWin Open Recovery image from http://techerrata.com/browse/twrp2/flo, which you should save into your
sdk\platform-tools folder\
- The latest SuperSU zip, from http://download.chainfire.eu/supersu, which you should save, on your Nexus device, in the "Downloads" folder, without extracting it (i.e. as a zip file). This file will be named something like "UPDATE-SuperSU-vX.YZ.zip".
For safety, once you have restored apps, settings and files, you should,
issue a complete poweroff. Then boot it back again, confirm that you have USB debugging running (The small Android icon at the top left corner) and, in the command prompt Window issue:
adb reboot bootloader
Now that we're back in the bootloader, we are going to
replace the stock recovery image, by
flashing the TWRP we just downloaded over it. Provided the TWRP file you downloaded above is named "recovery openrecovery-twrp-2.6.3.0-flo.img", the command you will need to issue:
fastboot flash recovery openrecovery-twrp-2.6.3.0-flo.img
Now you need to reboot in recovery mode. You can do that by using Volume Up/Down until "Recovery Mode" is displayed at the top, and then pressing Power.
You should be greeted with the following screens:
Once you see the above, tap "Install" and select the "UPDATE-SuperSU-vX.YZ.zip" you should have in your "Download" folder:
You should then see the following:
At this stage, you should proceed to swipe, to install the files contained in the zip into the OS partition. What this process actually does is copy two executables
su and
chattr (Change Attribute) in your
/system/xbin/ directory, as well as install a daemon that, will be launched at boottime.
You can then proceed to reboot the device, by selecting "Reboot" on the initial screen and then "System".
Installing BusyBox
Now that we have the system part of SuperSU installed, we can go to the Play Store and install the SuperSU client app, so just go ahead and do that.
Congratulations! At this stage, you have supposedly completed the hardest part, and your device is effectively rooted.
First thing you probably want to do then, is confirm that this is actually the case by installing "Root Checker" from the Play Store. If you launch it and click on the "Verify Root Access" you should get a prompt such as this one:
This is a SuperSU prompt, one that you should become exceedingly familiar with as you install more apps that request root access. When you see it, you should tap on "Grant", and after that, Root Checker should confirm that you have root access indeed.
Alrighty, moving on to our next target. We're of course not going to be sitting around installing rooted apps all day. What we want is an actual Linux shell, that we can access remotely. Thus, the first application we want to install is Busybox, that provides a basic set of base Linux utilities, as well as a basic shell.
On to the Play Store it is. If you search for BusyBox, you'll find a bunch of 'em. The one I installed was the free version from Stephen Ericson (
Stericson) that will probably be the first result you'll see.
After it's installed, you should run the app, let it scan your system for a bit, and then go for the Smart Install. In the process, you will be greeted by another "Superuser request" prompt from SuperSU, which you should of course grant.
Once we've done that, and to confirm that BusyBox is properly installed, we're can to go back to our Windows prompt and issue:
adb shell
This opens an interactive shell on our Linux box (with a terminal that sucks, but we're not going to worry about that). You can then confirm that BusyBox was properly installed by issuing the command
busybox. The result you get should be similar to this:
shell@flo:/ $ busybox
busybox
BusyBox v1.21.1-Stericson (2013-07-08 15:58:11 BST) multi-call binary.
BusyBox is copyrighted by many authors between 1998-2012.
Licensed under GPLv2. See source distribution for detailed
copyright notices.
Usage: busybox [function [arguments]...]
or: busybox --list[-full]
or: busybox --install [-s] [DIR]
or: function [arguments]...
BusyBox is a multi-call binary that combines many common Unix
utilities into a single executable. Most people will create a
link to busybox for each function they wish to use and BusyBox
will act like whatever it was invoked as.
Currently defined functions:
[, [[, ash, awk, base64, basename, blkid, bunzip2, bzcat, bzip2, cal,
cat, chat, chattr, chgrp, chmod, chown, chroot, chrt, cksum, clear,
comm, cp, crond, crontab, cut, date, dd, depmod, devmem, df, diff,
dirname, dmesg, dnsd, dnsdomainname, dos2unix, du, echo, egrep, env,
ether-wake, expand, expr, fakeidentd, fdflush, fdformat, fdisk, fgrep,
find, fold, free, freeramdisk, fsck, fsync, ftpd, ftpget, ftpput,
fuser, getopt, grep, groups, gunzip, gzip, hd, head, hexdump, hostid,
hostname, httpd, hwclock, id, ifconfig, ifenslave, inetd, inotifyd,
insmod, install, ionice, iostat, ip, ipaddr, ipcalc, iplink, iproute,
iprule, iptunnel, kill, killall, killall5, less, ln, logname, losetup,
ls, lsattr, lsmod, lsof, lsusb, lzop, lzopcat, md5sum, microcom, mkdir,
mkdosfs, mke2fs, mkfifo, mkfs.ext2, mkfs.vfat, mknod, mkswap, modinfo,
modprobe, more, mount, mountpoint, mt, mv, nameif, nanddump, nandwrite,
nc, netstat, nice, nmeter, nslookup, ntpd, od, patch, pgrep, pidof,
ping, ping6, pkill, pmap, powertop, printenv, printf, ps, pscan, pwd,
rdate, rdev, readahead, readlink, realpath, renice, reset, rev, rfkill,
rm, rmdir, rmmod, route, run-parts, script, scriptreplay, sed, seq,
setkeycodes, setlogcons, setsid, sha1sum, sha256sum, sha3sum,
sha512sum, showkey, sleep, smemcap, sort, split, start-stop-daemon,
stat, strings, stty, sum, swapoff, swapon, sync, sysctl, tac, tail,
tar, tee, telnet, telnetd, test, tftp, tftpd, time, timeout, top,
touch, tr, traceroute, traceroute6, tty, ttysize, tunctl, umount,
uname, uncompress, unexpand, uniq, unix2dos, unlzop, unzip, uptime,
usleep, uudecode, uuencode, vconfig, vi, watch, wc, wget, which, who,
whoami, whois, xargs, zcat
shell@flo:/ $
Looks good enough. Now you can type
exit to exit the shell and go back to the Windows command prompt.
And since we're done with the Windows command, you may want to issue:
adb kill-server
So that you can later disconnect your device without Windows complaining about it.
Installing an SSH server
At last, we've come to the final piece of our puzzle! Surprisingly, if you visit the Play Store, you'll find that there aren't that many SSH servers on offer.
The one I picked then is "Rooted SSH/SFTP Daemon", which looks a bit basic but does its job very well.
Once you launch it, tap the gear icon in the middle of the screen, and change at least the Login ID (I used 'root') and Password. You probably also want to enable "Wifi Lock" so that the SSH server will keep running in the background as you switch apps.
Now you want to press the large ON/OFF button so that it is highlighted red and so that our server is running. You should also get a small grey round ON/OFF icon in the top left area (see previous or next screenshot). Oh, and you'll probably have gotten another SuperSU grant request at this stage.
"Well, I seem to have an SSH server running alright, you say, but how do I find the name or IP address I should use to connect to it?"
The simplest method, without having to install another app or check your Wifi router, is to swipe down the Wifi icon in the top right corner and tap the Wifi properties.
Oh yeah, did you know that, if you swipe down any of the small status icons that appear at the top, you can quickly access the application and settings behind them? That's a good trick to know, and I sure didn't.
In this case, you'll be able to tap your current Wifi connection and get the IP address you need to use for SSH:
Give a go to that IP address in an ssh client, such as putty, and lo and behold, you should be connected to your Nexus 2013 Android device under a nice shiny shell. That's more like it!
Customizing our GNU/Linux Android system
Let's now push things to their logical conclusion, by performing 2 last items:
- As you may have noticed if you scan your network, and if you let the DHCP client provide its desired hostname, your Nexus 7 will be identified as 'android_12345678' or something. Ugh, let's change that!
- Edit that
/etc/hosts to filter ads, as we said we'd do.
With regards to item 1, a quick search tells us that the file we want to edit is
/system/build.prop, where you want to add a
net.hostname=my_name line. So you go ahead and try that, only to find that the file is read-only?!?
What gives? Weren't we supposed to be root here?
Well, that's Android security for ya (which may or may not be that bad a thing). By default, only the directories under
/sdcard (such as "Download" and stuff) are read/write. The rest of the system is read-only.
Fixing this is easy though. If you want to modify system files then, you just need to issue the following to be granted full read/write access:
mount -o rw,remount -t rootfs /system
Much better!
Now you can edit your
/system/build.prop to your hearts content and change the DHCP hostname.
Let's finish the job by going ads busting then. Still from the ssh shell:
cd /sdcard/Download
wget http://winhelp2002.mvps.org/hosts.zip
unzip hosts.zip
mv HOSTS hosts
dos2unix hosts
cp hosts /etc/
The last line will overwrite the existing
/etc/hosts, which is fine since it only contains one entry to alias
127.0.0.1 to
localhost (which is also present in the new file). Oh, and the
dos2unix is necessary as the original
HOSTS file was saved in DOS mode.
Do that, try to surf, and watch in awe as the ads pollution has now gone away...
I think my work here is done...